 pmeerw's blog
pmeerw's blog
 pmeerw's blog
pmeerw's blog
Jan 2019
git am on Windows
Note to self: on Windows use git am --whitespace=nowarn --keep-cr to apply commits
previously created by format-patch. WTF?
posted at: 16:32 | path: /programming | permanent link
Finally, I decided to give DNSSEC a try, the technology should be somewhat mature by now...
So I'm using bind 9.11.5 on Debian buster to secure pmeerw.at. I loosely followed the Debian DNSSEC HOWTO. DNSViz has been useful for testing.
Create a directory /etc/bind/keys
Enable DNSSEC in /etc/bind/named.conf.options and set the key directory:
options {
// ...
dnssec-enable yes;
key-directory "/etc/bind/keys";
}
The bind9utils package has the dnssec-keygen tool, so run:
cd /etc/bind/keys dnssec-keygen -a RSASHA256 -b 2048 -3 pmeerw.at dnssec-keygen -a RSASHA256 -b 2048 -3 -fk pmeerw.atto obtain the following files:
-rw-r--r-- 1 bind bind 601 Jan 22 22:31 Kpmeerw.at.+008+14644.key -rw------- 1 bind bind 1776 Jan 22 22:31 Kpmeerw.at.+008+14644.private -rw-r--r-- 1 bind bind 602 Jan 22 22:32 Kpmeerw.at.+008+49161.key -rw------- 1 bind bind 1776 Jan 22 22:32 Kpmeerw.at.+008+49161.privateI have set ownership of
keys/ to bind:bind, so: chown -R bind:bind /etc/bind/keys/
The zone pmeerw.at is configured in /etc/bind/named.conf.local:
zone "pmeerw.at" {
type master;
file "/etc/bind/db.pmeerw.at";
auto-dnssec maintain;
inline-signing yes;
};
Restart the nameserver: service bind9 restart
Use dig @127.0.0.1 +dnssec pmeerw.at axfr and RRSIG, NSEC records should be displayed for the zone.
Zone transfers (AXFR) must be allowed, at least for localhost:
options {
// ...
allow-transfer {
127.0.0.1;
};
}
I'm using Joker; in case the authoritative nameserver is already configured correctly for DNSSEC, joker.com's web-based administration interface already has all the
required fields completed:
alg: 8, digest: 5C09567DA17552239455C597878F97CCABDDBF6E, digest type: 1 (or 2), keytag: 14644
In order to get these values, the dnssec-dsfromkey tool is helpful:
dnssec-dsfromkey /etc/bind/keys/Kpmeerw.at.+008+14644.key
pmeerw.at. IN DS 14644 8 1 5C09567DA17552239455C597878F97CCABDDBF6E pmeerw.at. IN DS 14644 8 2 E2085DD26A5BE04722BCE5DEC62CA739919CCE9B8743800610142B7AF4BB2080The listing shows the DS records that would be configured in the .at nameserver; it provides us with the keytag (14644), algorithm (8 for RSA/SHA256, see list), digest type (1 for SHA-1, 2 for SHA-256, see list) and the digest value.
I had to limit UDP packet sizes to 512 in
/etc/bind/named.conf.options, otherwise
IPv6 showed transmission problems and delays -- not fully investigated yet, some related info
options {
// ...
edns-udp-size 512;
max-udp-size 512;
}
DNSViz results for pmeerw.at:
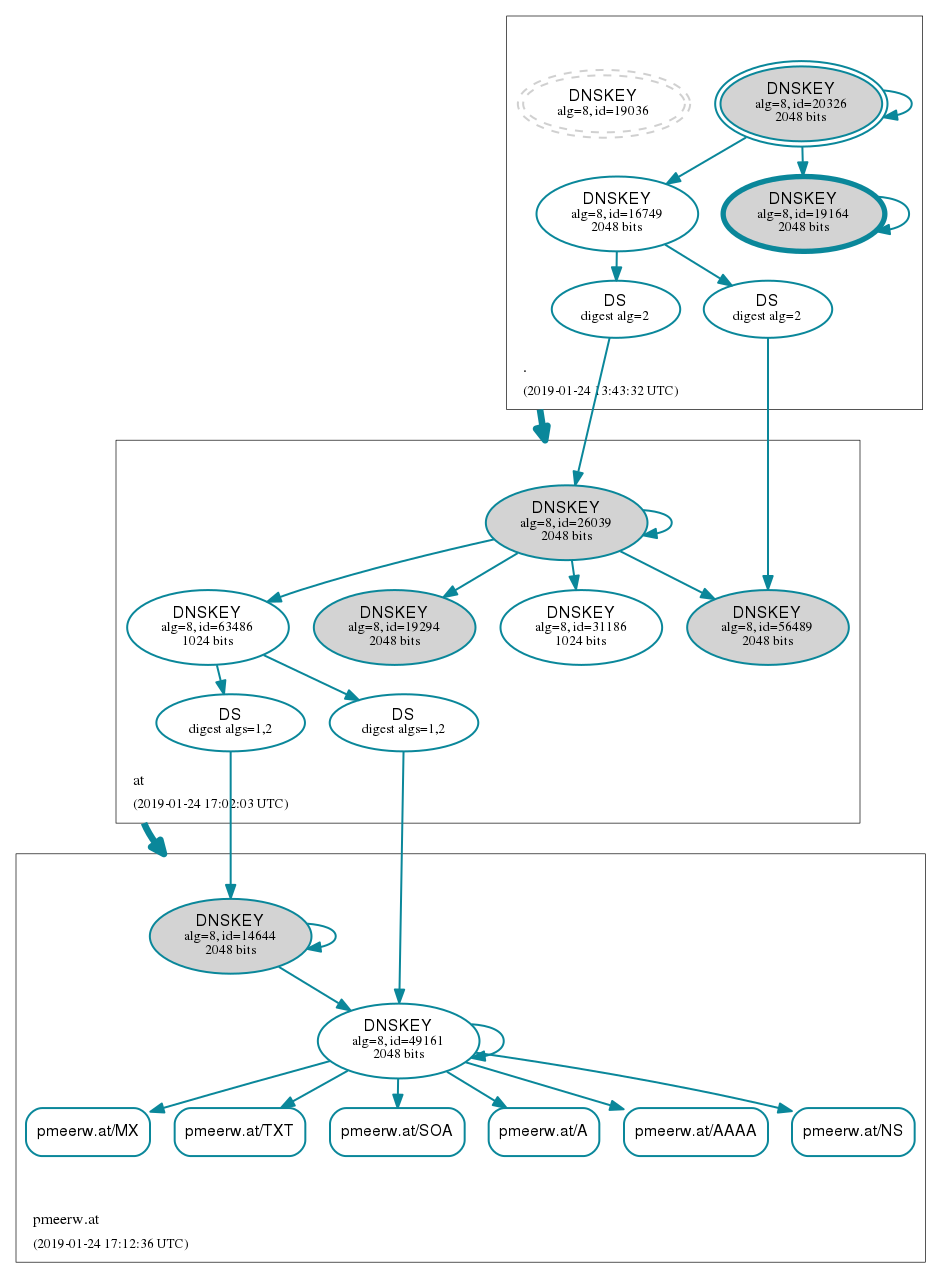
See also DNSSEC-analyzer results.
posted at: 19:31 | path: /configuration | permanent link