 pmeerw's blog
pmeerw's blog
 pmeerw's blog
pmeerw's blog
Dec 2022
Got a 11x44 LED badge labelled S1144. It identifies as
usb 1-2: new full-speed USB device number 61 using xhci_hcd usb 1-2: New USB device found, idVendor=0416, idProduct=5020, bcdDevice= 1.00 usb 1-2: New USB device strings: Mfr=1, Product=2, SerialNumber=0 usb 1-2: Product: CH546 usb 1-2: Manufacturer: wch.cn hid-generic 0003:0416:5020.0090: hiddev1,hidraw2: USB HID v1.00 Device [wch.cn CH546] on usb-0000:02:00.0-2/input0The CH546 is a 8051 MCU. It uses a USB HID interface. There is some Windows software to program it.
Here's what lsusb -v -v -v has to say about it:
Bus 001 Device 062: ID 0416:5020 Winbond Electronics Corp. CH546
Device Descriptor:
bLength 18
bDescriptorType 1
bcdUSB 1.10
bDeviceClass 0
bDeviceSubClass 0
bDeviceProtocol 0
bMaxPacketSize0 64
idVendor 0x0416 Winbond Electronics Corp.
idProduct 0x5020
bcdDevice 1.00
iManufacturer 1 wch.cn
iProduct 2 CH546
iSerial 0
bNumConfigurations 1
Configuration Descriptor:
bLength 9
bDescriptorType 2
wTotalLength 0x0029
bNumInterfaces 1
bConfigurationValue 1
iConfiguration 4 wch.cn
bmAttributes 0xa0
(Bus Powered)
Remote Wakeup
MaxPower 70mA
Interface Descriptor:
bLength 9
bDescriptorType 4
bInterfaceNumber 0
bAlternateSetting 0
bNumEndpoints 2
bInterfaceClass 3 Human Interface Device
bInterfaceSubClass 0
bInterfaceProtocol 0
iInterface 5 wch.cn
HID Device Descriptor:
bLength 9
bDescriptorType 33
bcdHID 1.00
bCountryCode 0 Not supported
bNumDescriptors 1
bDescriptorType 34 Report
wDescriptorLength 34
Report Descriptor: (length is 34)
Item(Global): Usage Page, data= [ 0x00 0xff ] 65280
(null)
Item(Local ): Usage, data= [ 0x01 ] 1
(null)
Item(Main ): Collection, data= [ 0x01 ] 1
Application
Item(Local ): Usage, data= [ 0x02 ] 2
(null)
Item(Global): Logical Minimum, data= [ 0x00 ] 0
Item(Global): Logical Maximum, data= [ 0x00 0xff ] 65280
Item(Global): Report Size, data= [ 0x08 ] 8
Item(Global): Report Count, data= [ 0x40 ] 64
Item(Main ): Input, data= [ 0x06 ] 6
Data Variable Relative No_Wrap Linear
Preferred_State No_Null_Position Non_Volatile Bitfield
Item(Local ): Usage, data= [ 0x02 ] 2
(null)
Item(Global): Logical Minimum, data= [ 0x00 ] 0
Item(Global): Logical Maximum, data= [ 0x00 0xff ] 65280
Item(Global): Report Size, data= [ 0x08 ] 8
Item(Global): Report Count, data= [ 0x40 ] 64
Item(Main ): Output, data= [ 0x06 ] 6
Data Variable Relative No_Wrap Linear
Preferred_State No_Null_Position Non_Volatile Bitfield
Item(Main ): End Collection, data=none
Endpoint Descriptor:
bLength 7
bDescriptorType 5
bEndpointAddress 0x82 EP 2 IN
bmAttributes 3
Transfer Type Interrupt
Synch Type None
Usage Type Data
wMaxPacketSize 0x0040 1x 64 bytes
bInterval 1
Endpoint Descriptor:
bLength 7
bDescriptorType 5
bEndpointAddress 0x02 EP 2 OUT
bmAttributes 3
Transfer Type Interrupt
Synch Type None
Usage Type Data
wMaxPacketSize 0x0040 1x 64 bytes
bInterval 1
Device Status: 0x0000
(Bus Powered)
posted at: 21:22 | path: /programming | permanent link
Another nice article showing off DNSSEC strength...
Generate SSHFP DNS records for by host (pmeerw.net):
$ ssh-keygen -r @ @ IN SSHFP 1 1 3b00267ed86c211026e6d8b8eb5d9a7d9e51cf7d @ IN SSHFP 1 2 189d464e8a13d2df66d882afdcb4220fb281ba1f19eda96aa35bf1a50188b0a7 @ IN SSHFP 2 1 adb06e3c4de279d2338bbec35a9a64c8661fb431 @ IN SSHFP 2 2 50e72d460ea86ad416b74b71f9b0c948bf42004ebf730290eff9d43fea9545a6 @ IN SSHFP 3 1 aaa45514f6bd534448ab7f09842fe1e13c269142 @ IN SSHFP 3 2 cc68f391aea002966cc3d7e84ce41dc73d4cfb6c2381e5b665f26603f8317dd3 @ IN SSHFP 4 1 7482ed5e3e6621978bd0bbd61f6b9740dcef252c @ IN SSHFP 4 2 eb77b6f29bee067d6524459e4cfc696881bd70908d514be682cb068746729594
SSH can silently connect to an SSH server (without asking to verify the host fingerprint!) if VerifyHostKeyDNS is enabled: ssh -o VerifyHostKeyDNS=yes pmeerw@pmeerw.net.
posted at: 22:58 | path: /configuration | permanent link
RFC7929 describes a way to put OpenPGP public keys into DNS using DANE. Here's an article which I shamelessly condense here...
There is a DNS resource record that stores the complete public key. I'm using ECC to bring down key size. It looks like this:
c746aa6d791946caf1aade6dc6c5e720e6e79d650e5b882dc11a2078._openpgpkey.pmeerw.net. IN OPENPGPKEY (
mDMEY54vtRYJKwYBBAHaRw8BAQdAmhK78RNv+Azsrrcgnb4Ijf4JwEOfHM8D
paY2yy1w0oG0KlBldGVyIE1lZXJ3YWxkLVN0YWRsZXIgPHBtZWVyd0BwbWVl
cncubmV0PoiQBBMWCAA4FiEE5u5nS8lBNCYy5igrw5J6UWK+XtEFAmOeL7UC
GwMFCwkIBwIGFQoJCAsCBBYCAwECHgECF4AACgkQw5J6UWK+XtE+dAD/dZAp
If2WWK2fAQgGIxOepBr6Nj2g6Z78W25wyYiSxvIA/1VtCuCsveRGmKZ0wnuQ
kJP4z3v+r/XdjRJeingYSnsKuDgEY54vtRIKKwYBBAGXVQEFAQEHQPCrzg3G
IRhYWFdUkps1DSqmLEZ5xQX6D96jYpq28Lp1AwEIB4h4BBgWCAAgFiEE5u5n
S8lBNCYy5igrw5J6UWK+XtEFAmOeL7UCGwwACgkQw5J6UWK+XtGQyQD/RD1d
zIk/Kjnb1yKcW+GAIHkpahgEQzpk7Bcxk38ReaAA/j2ZoXGMeMNVlJdOIv7d
gr/Hw9ygwxInPg9Nth2wpKoB
)
The name part is the SHA-256 hash of "pmeerw". You can use the command openpgpkey --create pmeerw@pmeerw.net to create the record (install the Debian/Ubuntu hash-slinger package).
Try openpgpkey.info to query a PGP public key!
posted at: 22:49 | path: /configuration | permanent link
Got a 16x16 Divoom Pixoo pixel art frame, a Bluetooth connected device with a small battery in a nice case. It can blink pixels. There's an app and Github repo with Python code.
Still, getting the think to run was a bit of a challenge on Ubuntu 22.04... First, it show up as a Bluetooth device:
$ hcitool scan Scanning ... 11:75:58:xx:xx:xx PixooThen, one can check if RFCOMM is available using
sdptool:
$ sdptool browse 11:75:58:xx:xx:xx
Browsing 11:75:58:xx:xx:xx ...
Service Name: Serial Port 1
Service RecHandle: 0x10004
Service Class ID List:
"Serial Port" (0x1101)
Protocol Descriptor List:
"L2CAP" (0x0100)
"RFCOMM" (0x0003)
Channel: 1
Note the channel number (1), older Divoom devices use (4) here.
Next, there's an issue with Ubuntu's python3-pybluez package (0.23-4build1) in 22.04/jammy:
self.sock.send(bytes(package)) File "It's an issue with Python 3.10 and apparently a special flag macro must be #defined when compiling the library. Luckily, this can be easily fixed by installing the python3-pybluez 0.23-5 package from 22.10/kinetic.", line 3, in send SystemError: PY_SSIZE_T_CLEAN macro must be defined for '#' formats
posted at: 13:11 | path: /fun | permanent link
OpenAI's chat is all the rage currently, so I have it a try with a well-known MBA expression: E=(x^y)+2*(x&y).
This should simplify (spoiler alert) to x+y, however...
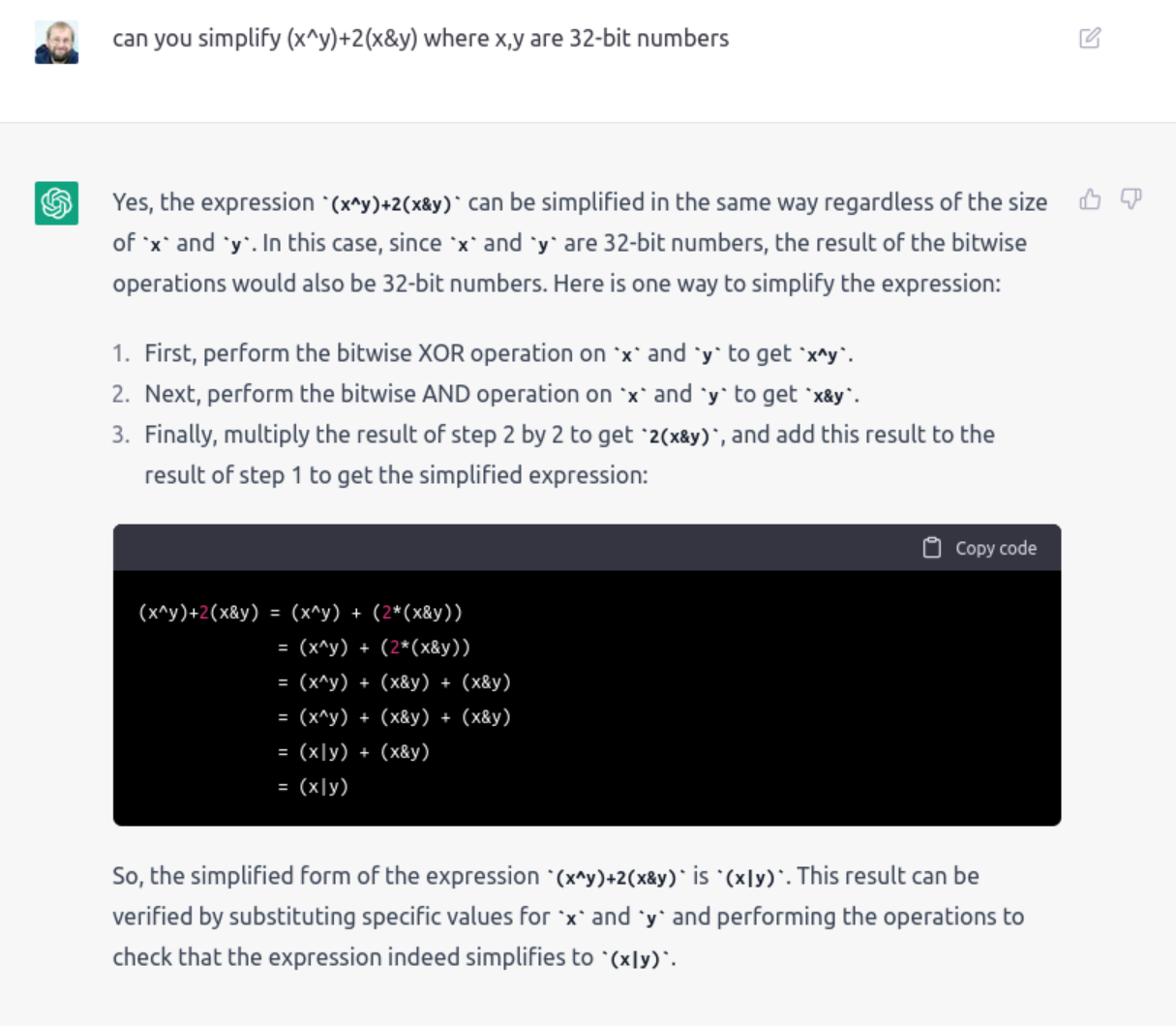
I'm not so convinced about the result, but nevertheless impressed by the answer. Also, I didn't quite get what the 'open' part in openai.com is...
posted at: 11:51 | path: /rant | permanent link