 pmeerw's blog
pmeerw's blog
 pmeerw's blog
pmeerw's blog
Aug 2024
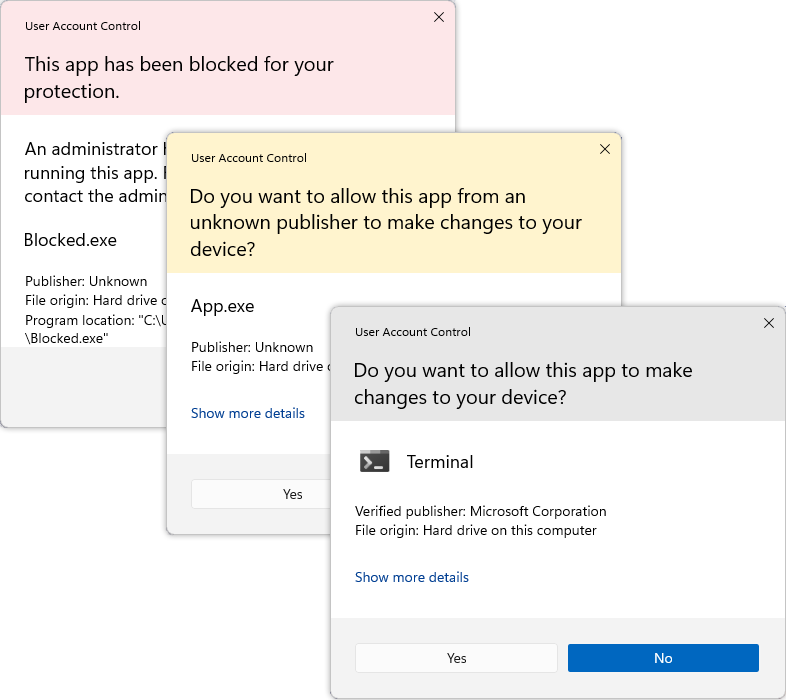
A signed Windows executable allows windows to display the publisher name in the UAC dialog, except sometimes it doesn't work. Windows uses Authenticode to verify the integrity of a PE32 executable and provide authentication via code signing.
One way to learn more what UAC does w.r.t. crypto is to enable CAPI2 diagnostics , i.e. event logging.
Things to remember: the entire certificate chain up to but not including the root CA's certificate should be in the executable, i.e. all intermediate certificate. When certificate are missing, they might be retrieved by Certificate Authority Information Access (AIA), specified in RFC5280 via some HTTP URLs given in the certificates.
Different applications implement different verification policies: caching of certifiates, revocation list checks, etc. It's know clear what checks Windows, or the UAC dialog, or other application do to check the authenticity of an executable.
Tooling is difficult: again, it's not clear what the verification policy is. For example, Microsoft's signtool does not complain about missing intermediate certificates.
Looking for some more mystery to research: Try page hashes!
posted at: 00:45 | path: /programming | permanent link